I have long been a fan of Hak5, I enjoy their videos and their content is informative and entertaining. I have also been curious about the various tools they have produced, from the Wifi Pineapple to the Rubber ducky they are well built and do their job well. When they introduced the Bash Bunny earlier this year I was even more intrigued. This was a linux computer that enabled physical attacks via USB that could emulate a HID device, RNDIS/ECM and USB storage. But, at $99USD + international postage it is a big expense that I just couldn’t justify.
A Mentor once said to me ‘Real hackers make their own tools’ and this I believe is true as it allows you to fully understand how the hardware and software work to produce the effects you are after. You can create a Wifi Pineapple from a Raspberry Pi, a few Alfa cards and FruityWifi. A rubber ducky can be built using a Malduino Bad USB, but the Bash Bunny was something that eluded me until I discoverd the P4wnP1 project by MaMe82.
P4wnP1
The P4wnP1 project utilises a Raspberry Pi zero and weaponsises it into a USB Attack Platform. Like the Bash Bunny, the P4wnP1 can emulate HID, USB Mass Storage and RNDIS/ECM. The project is based of Rasbian Jesse or Stretch and payloads are developed utilising pure Bash. The real highlight of the project was the development of the Windows Lockpicker payload, which took advantage of Mubix’s stealing creds from a locked machine exploit and combined it with a hash crack using John the ripper. The result was the ability of the P4wnP1 to obtain a simple Windows 10 hash, crack it, enter it into the password prompt and access the locked computer (as demonstrated by this YouTube video). The P4wnP1 also takes advantage of the Wifi and bluetooth features of the Raspberry Pi Zero W and allows you to create a backdoor to a PC with a shell via Wifi. This has obvious advantages such as getting access to Air Gapped machines from within range of the Raspberry Pi’s wifi capabilities.
The P4wnP1 also utilises the Duck Encoder that allows it to read in and process Ducky Script. This makes it easily to convert already existing Bash Bunny scripts into the format that is required for P4wnP1.
Hardware
As it is, the P4wnP1 connects to a computer using the Raspberry Pi Zero’s data micro-usb port. This allows it to be powered and to send data. However, connecting a mico-usb cable with a Raspberry Pi Zero hanging off it is very easy and this is where the Bash Bunny wins out. The Bash Bunny is built like a USB Drive that can be easily plugged in and out. Also, the P4wnP1 only allows you to only have one payload whereas the Bashbunny has a three way switch that allows you to set two payloads an an arming mode. So the answer was to modify the Raspberry Pi to make it more Bash Bunny like.
I first set about adding a male USB adapter to allow me to plug the Raspberry Pi directly to my computer with the need for a cable. I had an old 1GB USB Drive laying around which no longer worked, So i desoldered the head off the drive and soldered it to the connection points on the underside of the Raspberry Pi.
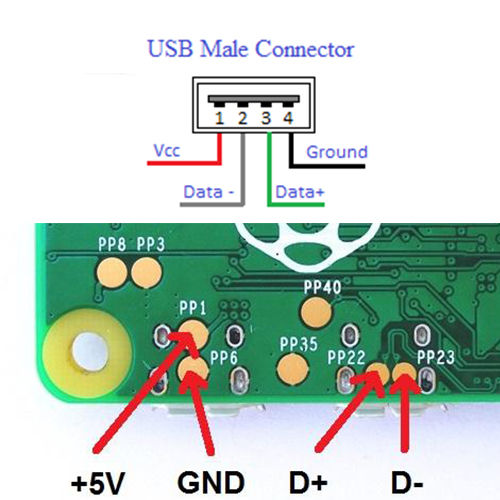
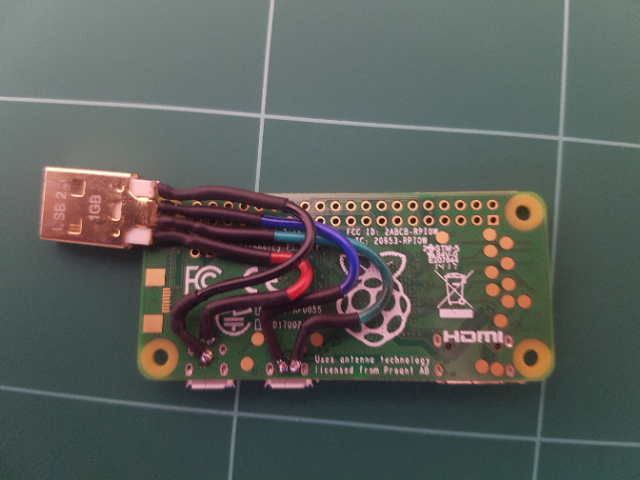
The next thing I needed to do was add a switch. My options were really limited to what is available at Jaycar. My options were further limited to my desire to keep the switch as low profile as possible so that the device was not too bulky. I finally decided on a 3-way DIP switch. This provided me with the added benefit of having up to 8 payloads.
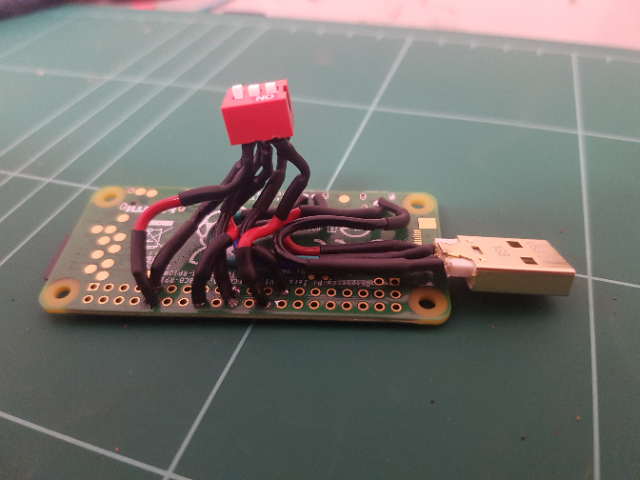
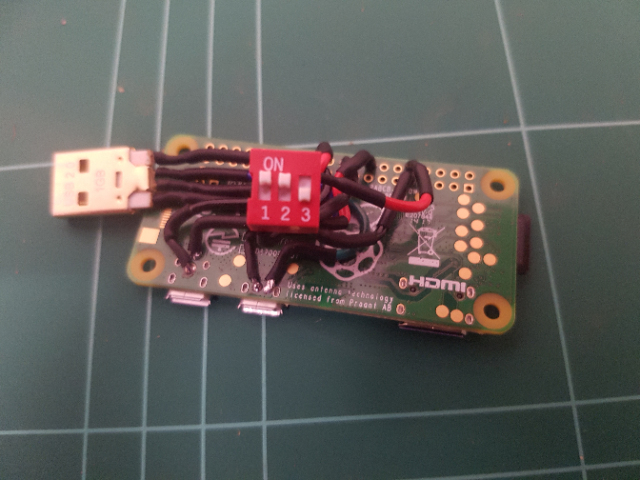
I soldered the switch to the GPIO pins on the Raspberry Pi and then knocked up the following script in python to read their values in.
#!/usr/bin/env python
import RPi.GPIO as GPIO
GPIO.setmode(GPIO.BOARD)
pins = [8,10,16]
for pin in pins:
GPIO.setup(pin, GPIO.IN, pull_up_down=GPIO.PUD_UP)
output = ''
for pin in pins:
if not GPIO.input(pin):
output+= '1'
else:
output += '0'
output = output[::-1]
print(output)Software
I made a number of changes to the configuration of P4wnP1 to meet my needs and essentially I was aiming to make a device that was as similar in use and function as the Bash Bunny. I had used a 32GB micro-sd card to flash Rasbian, so I had a lot of space available to me. Therfore I modified the install.sh script to create a 16GB USB Storage file, I then formatted the image file to be ExFat instead of Fat32. I then modified the setup.cfg file to mount the USB Storage file during start up and to use that as the location for my payloads. I created ‘Switch’ folders inside a payload directory and modified all existing P4wnP1 payloads to be named ‘payload.txt’ to allow them to be easily read depending on which Switch folder they were in. The reason for mounting the USB Image file was so that I could create an ‘Arming’ mode that allowed me to plug in the P4wnP1 in any computer and modify and change payloads. As the existing way under the P4wnP1 project meant I had to SSH into the device to change payloads via the command line (not as friendly and as simple as the Bash Bunny).
Mounting the USB Image file does create some issues and when creating payloads I need to take care of when you are accessing the storage as USB Mass storage (via a computer) or when mounted via the Linux file system. This can cause some corruption issues, however there has been nothing significant other than the usual ‘Windows needs to scan and repair this drive’ warnings. It is important that Payloads unmount the drive at the end of their payloads, as this can cause other issues as well. But, with careful management this can be a non-issue.
I also installed Samba and created a network share. This creates a new way of extracting files from a computer which can have added benefits over transfer via USB Mass Storage. The Samba share accesses the linux file system directly, therefore commands can be run via the Linux system to check if files exist or have been transferred. Trasnfer of USB Mass Storage does not sync until there is an unmount or the drive is disconnected. So if files need to be checked or moved via the File system, the network share is a useful feature.
Payloads
I have created a number of payloads, that range from File Extraction, Mimikatz clear text password extraction, Stealing creds from Windows Password vault as well as a conversion of a couple of Bash Bunny payloads. My payloads are available on my GitHub and I will be adding more as I develop them.
Comparison to the Bash Bunny
The first thing when looking at a comparison of the Bash Bunny and P4wnP1 is the cost. In total the P4wnP1 cost me $30AUD, where as the Bash Bunny is $99USD. The P4wnP1 has Wifi and Bluetooth and the Bash Bunny does not. The P4wnP1 is open source and I can create, modify and do what I want to the software, where the Bash Bunny is closed source and reliant on Hak5 for firmware upgrades. The biggest detractor to the P4wnP1 is its appearance. Where the Bash Bunny wins is that it looks like a chunky USB drive. This is beneficial for penetration testing where you could hand the device over to someone to ‘print your resume’ and have a payload execute. Or if you are caught with it in a PC, you can pass it off as a USB Drive. My P4wnP1, looks suspicious and it looks like a Hacker tool (in same ways that is cooler), but when you consider how most of the payloads are executed and what their intentions are, they rely on physical access and penetration tester plugging it in themselves on an unlocked machine. So really, although it may be uglier the P4wnP1 can still get the job done. The following table was created by MaMe82 to compare the Bash Bunny to the P4wnP1. I have added my modifcations to the table as well.
| Feature | BashBunny | P4wnP1 |
|---|---|---|
| RNDIS, CDC ECM, HID , serial and Mass storage support | supported, usable in several combinations, Windows Class driver support (Plug and Play) in most modes | supported, usable in most combinations, Windows Class driver support (Plug and Play) in all modes as composite device |
| Target to device communication on covert HID channel | no | Raw HID device allows communication with Windows Targets (PowerShell 2.0+ present) via raw HID</br> There’s a full automated payload, allowing to access P4wnP1 bash via a custom PowerShell console from target device (see ‘hid_frontdoor.txt’ payload). </br> An additional payload based on this technique, allows to expose a backdoor session to P4wnP1 via HID covert channel and relaying it via WiFi/Bluetooth to any SSH capable device (bridging airgaps, payload ‘hid_backdoor.txt’) |
| Mouse emulation | no | Supported: relative Mouse positioning (most OS, including Android) + ABSOLUTE mouse positioning (Windows); dedicated scripting language “MouseScript” to control the Mouse, MouseScripts on-demand from HID backdoor shell |
| Trigger payloads via target keyboard | No | Hardware based: LEDs for CAPSLOCK/SCROLLLOCK and NUMLOCK are read back and used to branch or trigger payloads (see hid_keyboard2.txt payload) |
| Interactive DuckyScript execution | Not supported | supported, HID backdoor could be used to fire scripts on-demand (via WiFi, Bluetooth or from Internet using the HID remote backdoor) |
| USB configuration changable during runtime | supported | will maybe be implemented |
| Support for RubberDucky payloads | supported | supported |
| Support for piping command output to HID keyboard out | no | supported |
| Switchable payloads | 3-way Hardware switch (2 Payloads) | 3-way DIP Switch (8 Payloads) |
| Interactive Login with display out | SSH / serial | SSH / serial / stand-alone (USB OTG + HDMI) |
| Performance | High performance ARM quad core CPU, SSD Flash | Low performance single core ARM CPU, SDCARD |
| Network interface bitrate | Windows RNDIS: 2 GBit/s</br>Linux/MacOS ECM: 100 MBit/s</br>Real bitrate 450 MBit max (USB 2.0) | Windows RNDIS: 20 GBit/s</br>Linux/MacOS ECM: 4 GBit/s (detected as 1 GBit/s interface on MacOS)</br>Real bitrate 450 MBit max (USB 2.0)</br>Here’s the needed P4wnP1 patch |
| LED indicator | RGB Led, driven by single payload command | mono color LED, driven by a single payload command |
| Customization | Debian based OS with package manager | Debian based OS with package manager |
| External network access via WLAN (relay attacks, MitM attacks, airgap bridging) | Not possible, no external interface | supported with Pi Zero W |
| SSH access via Bluetooth | not possible | supported (Pi Zero W) |
| Connect to existing WiFi networks (headless) | not possible | supported (Pi Zero W) |
| Shell access via Internet | not possible | supported (WiFi client connection + SSH remote port forwarding to SSH server owned by the pentester via AutoSSH) |
| Ease of use | Easy, change payloads based on USB drive, simple bash based scripting language | Medium, bash based event driven payloads, inline commands for HID (DuckyScript and ASCII keyboard printing, as well as LED control) |
| Available payloads | Fast growing github repo (big community) | Slowly growing github repo (spare time one man show ;-)) Edit: Growing community, but no payload contributions so far |
| In one sentence … | “World’s most advanced USB attack platform.” | A open source project for the pentesting and red teaming community. |
| Total Costs of Ownership | $99USD | $20AUD for Raspberry Pi Zero W, USB A Connector (Free), $1.25 for 3-Way DIP Switch, $4 for Raspberry Pi Zero case. |


The Name
Your probably wondering, why I have called my variant the P4wnP1-Bilby. Well the Bilby is an Australian Marsupial with large ears, a tail and it hops. When you describe a Bilby to someone who has never seen one, the description sounds very much like a Bunny. However when you see the two together it is quite obvious that they are different. I think it describes my project quite well.